TheCCST Cybersecurity Study Guidedescribes theDiamond Model of Intrusion Analysisas a framework to map the relationships between four core features of an intrusion:
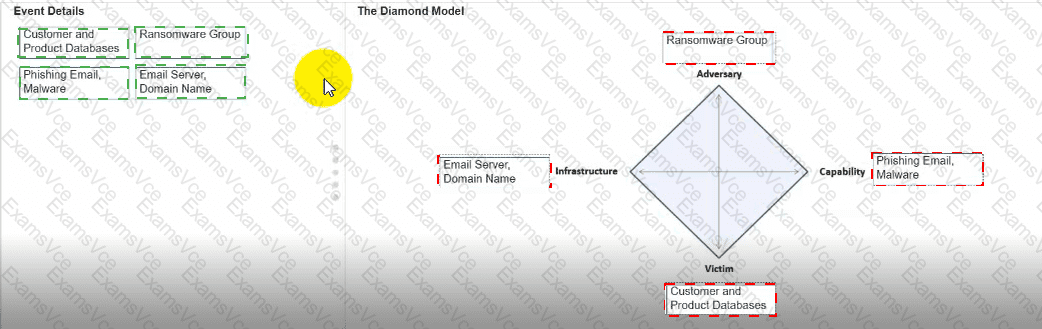
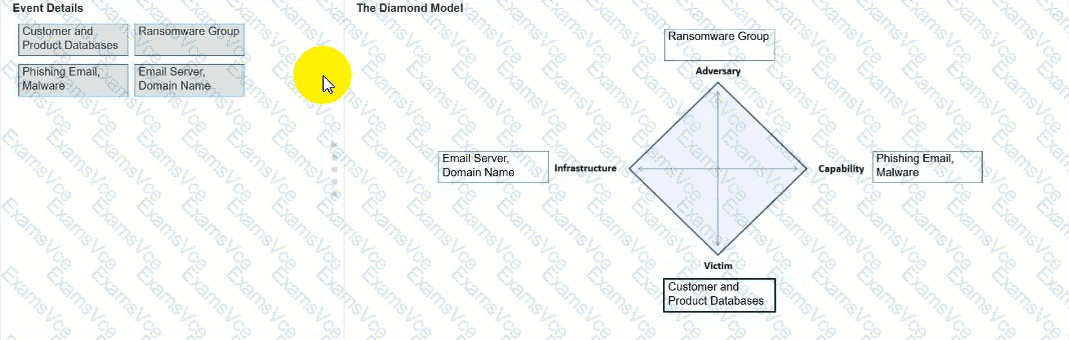
Example: Ransomware Group
Capability– The tools, techniques, or malware the adversary uses.
Example: Phishing Email, Malware
Example: Email Server, Domain Name
Victim– The target of the attack, such as systems, organizations, or individuals.
Example: Customer and Product Databases
"The Diamond Model helps analysts connect the attacker, the tools they use, the infrastructure supporting the attack, and the victim, providing a holistic view of the intrusion event."
(CCST Cybersecurity,Incident Handling, Threat Modeling section, Cisco Networking Academy)