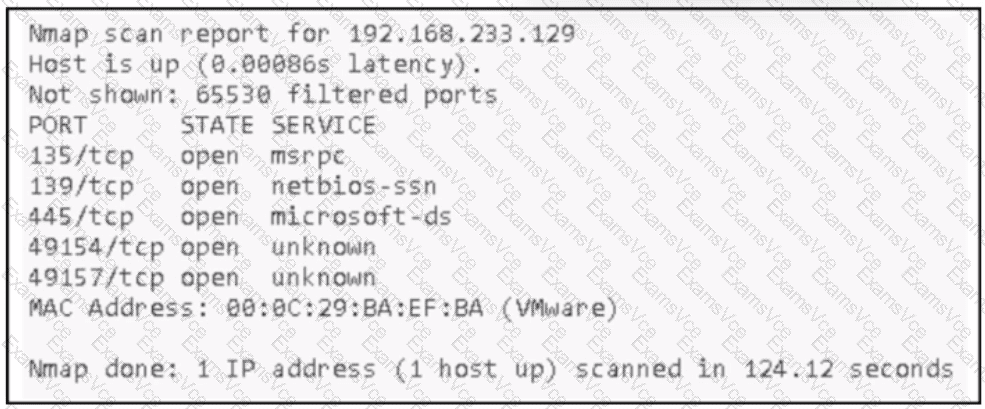
Lateral movement relies heavily on reconnaissance to identify systems, services, and attack paths inside a compromised network. The Nmap scan in the exhibit reveals open ports and associated services, which directly support this objective.
Option A is correct because identifying the function and service the server is providing allows the attacker to understand the system’s role. Services such as msrpc, netbios-ssn, and microsoft-ds strongly indicate a Windows host offering file sharing, remote procedure calls, and domain-related services. This information helps attackers select appropriate exploits, credential theft techniques, or privilege escalation paths.
Option C is also correct because running services and open ports are one of the most valuable outputs of a network scan. Open ports such as 135, 139, and 445 expose services that are commonly targeted for lateral movement using techniques like SMB relay attacks, Pass-the-Hash, or exploitation of known vulnerabilities.
Option B is incorrect because CPU details and vendor versions are not revealed in this scan output. Option D is incorrect because Nmap does not enumerate logged-in user security identifiers. Option E is incorrect because latency values are not used for command injection planning in lateral movement scenarios.
Therefore, the two scan elements that assist the attacker are the server’s function and its running services and ports.