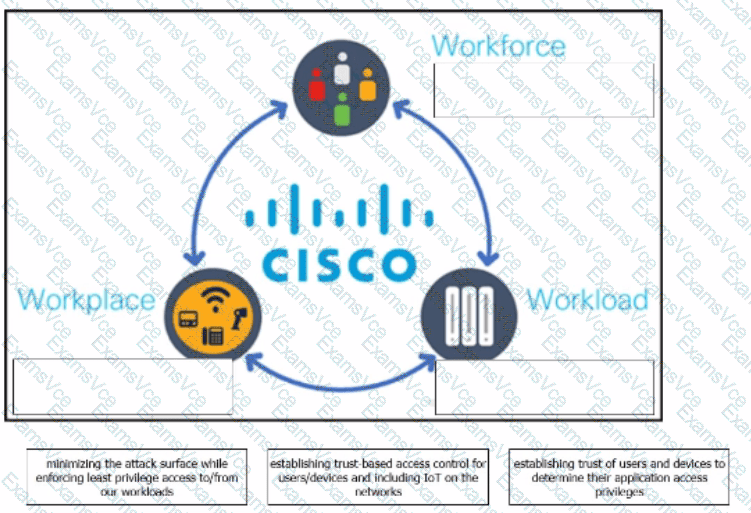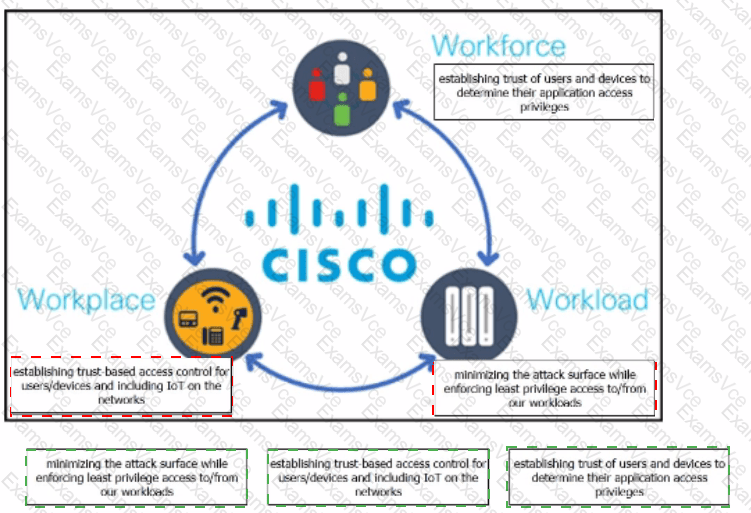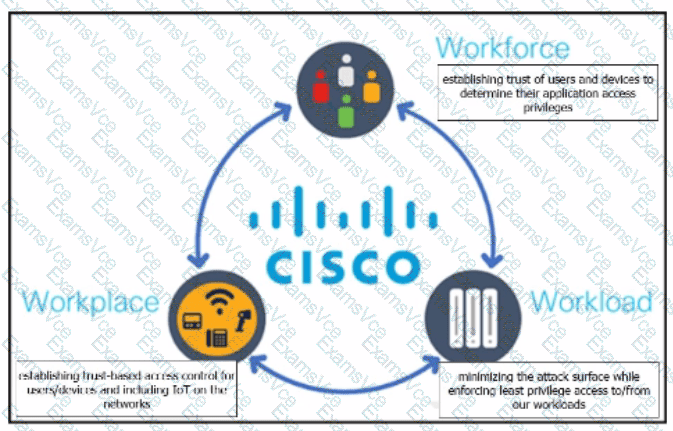
Cisco’s Zero Trust Architecture is built around the principle of never trust, always verify, and it organizes zero trust controls into three interconnected domains: Workforce, Workplace, and Workload. Each domain addresses a different aspect of access control and risk reduction.
The Workforce pillar focuses on user identity and endpoint posture. Cisco zero trust ensures that users and their devices are continuously verified before granting access to applications. This includes validating identity, device health, and context to determine appropriate access privileges.
The Workplace pillar addresses the network environment where users and devices connect. This includes enterprise networks, branch offices, and IoT environments. Cisco applies trust-based access controls to ensure that only authorized and compliant devices can communicate on the network, regardless of location.
The Workload pillar protects applications and services running in data centers, cloud environments, and containers. The goal is to reduce the attack surface by enforcing least-privilege access, ensuring that workloads only communicate with explicitly authorized services and users.
Cybersecurity operations documentation emphasizes that effective zero trust requires visibility and enforcement across all three areas. Cisco’s model simplifies implementation by clearly defining responsibilities and controls within each domain, enabling organizations to reduce lateral movement, limit blast radius, and improve overall security posture.