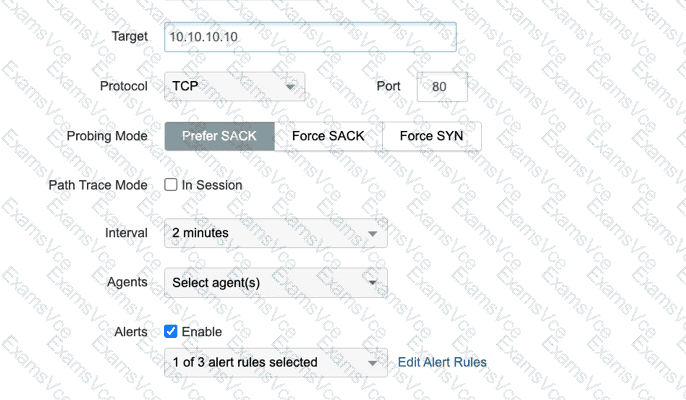
In theDesigning and Implementing Enterprise Network Assurance (300-445 ENNA)architecture, a critical challenge in active synthetic monitoring is ensuring that test probes accurately reflect user traffic without being dropped by intermediate security appliances. Standard network tests often utilize separate connections for measuring performance metrics (latency/loss) and for path discovery (hop-by-hop visualization). This behavior can be flagged by stateful firewalls or Intrusion Prevention Systems (IPS) as suspicious or malicious scanning activity.
To mitigate this, the engineer should enablePath Trace Mode: In Session(Option A). When this mode is active, ThousandEyes performs path discovery using the exact same TCP session established for the performance measurement. By embedding path discovery probes within an active, established session, the traffic appears to firewalls as part of a legitimate, ongoing communication stream rather than an independent series of probes with varying TTL values that might trigger "anti-spoofing" or "scanning" alerts.
Reviewing the alternative options:
Protocol: TCP (Option B):While using TCP is generally more firewall-friendly than ICMP, the exhibit shows TCP is already selected. The issue is not the protocol itself, but how the path discovery probes are handled relative to the session.
Port: 5000 (Option C):Changing the port to a non-standard value like 5000 often makes trafficmorelikely to be scrutinized or blocked by default firewall policies compared to standard web ports like 80.
Probing Mode: Force SYN (Option D):Forcing SYN packets is a technique used to bypass certain types of load balancers but does not address the fundamental issue of path discovery probes being seen as a separate, malicious scan by stateful inspection engines.
Therefore, enablingIn Sessionpath trace mode is the most effective way to ensure consistent visibility through security-hardened environments.