ECCouncil 412-79v10 Question Answer
Attackers create secret accounts and gain illegal access to resources using backdoor while bypassing the authentication procedures. Creating a backdoor is a where an attacker obtains remote access to a computer on a network.
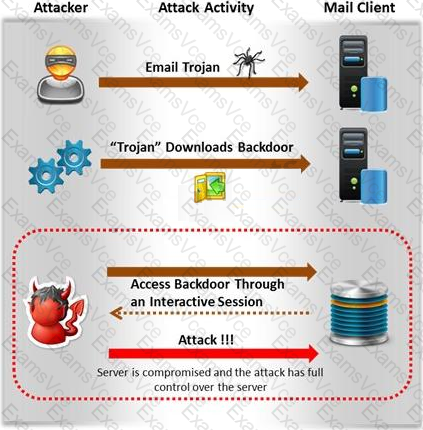
Which of the following techniques do attackers use to create backdoors to covertly gather critical information about a target machine?
ECCouncil 412-79v10 Summary
- Vendor: ECCouncil
- Product: 412-79v10
- Update on: Feb 7, 2026
- Questions: 201



