ECCouncil 412-79v10 Question Answer
The Web parameter tampering attack is based on the manipulation of parameters exchanged between client and server in order to modify application data, such as user credentials and permissions, price and quantity of products, etc.
Usually, this information is stored in cookies, hidden form fields, or URL Query Strings, and is used to increase application functionality and control. This attack takes advantage of the fact that many programmers rely on hidden or fixed fields (such as a hidden tag in a form or a parameter in a URL) as the only security measure for certain operations.
Attackers can easily modify these parameters to bypass the security mechanisms that rely on them.
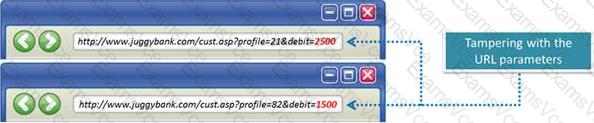
What is the best way to protect web applications from parameter tampering attacks?
ECCouncil 412-79v10 Summary
- Vendor: ECCouncil
- Product: 412-79v10
- Update on: Feb 8, 2026
- Questions: 201



