The problem states:
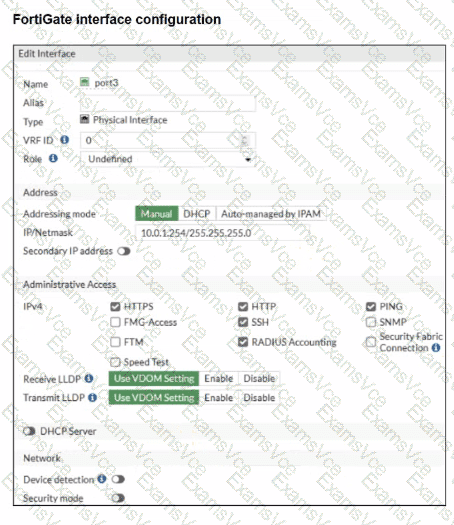
FortiGate receivesRADIUS accounting messagesonport3.
User-Nameattribute contains the username.
Classattribute contains the group membership.
Goal: authenticate users through RSSO and map them to the correct user groups.
To achieve this, three critical components must be configured:
✔A. RADIUS Attribute Value in the RSSO group must match the Class attribute
This is mandatory because:
RSSO user groups on FortiGate match users based onthe value inside the RADIUS attribute(usually Class).
For group assignment to work, FortiGate must compare:
RSSO User Group → RADIUS Class Attribute Value
This isexactly how FortiGate maps RSSO users to groups.
✔D. RSSO agent’s sso-attribute must be set to Class
Thesso-attributedefineswhich RADIUS attribute contains the group information.
Because group membership is carried in:
➡Class attribute
You must configure:
config user radius
set sso-attribute Class
end
This tells FortiGate:
"Use the Class attribute to derive user group membership."
✔E. rsso-endpoint-attribute must be set to User-Name
This identifieswhich RADIUS attributecarries the actualusername.
In this scenario:
RADIUS accounting messages contain the username inUser-Name.
So the correct setting is:
config user radius
set rsso-endpoint-attribute User-Name
end
This ensures the RSSO user object uses the correct username.
❌Incorrect Options Explained
B. Assign RSSO user groups to all firewall policies
Not required.
You only assign them to policies where RSSO authentication is used.
C. Device detection and Security Fabric Connection should be enabled on port3
Totally irrelevant to RSSO.
RSSO only needs RADIUS accounting, not device detection or Fabric services.