GIAC GPPA Question Answer
An attacker changes the address of a sub-routine in such a manner that it begins to point to the address of the malicious code. As a result, when the function has been exited, the application can be forced to shift to the malicious code. The image given below explains this phenomenon:
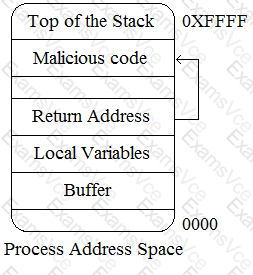
Which of the following tools can be used as a countermeasure to such an attack?
GIAC GPPA Summary
- Vendor: GIAC
- Product: GPPA
- Update on: Feb 7, 2026
- Questions: 285



