Comprehensive and Detailed Explanation From FortiSOAR 7.6., FortiSIEM 7.3 Exact Extract study guide:
In the context of theAttack Surface Managementmodules within theFortiSIEM 7.3andFortiSOAR 7.6security frameworks, "reducing the attack surface" refers to the process of minimizing the number of possible entry points (attack vectors) that an unauthorized user could exploit.
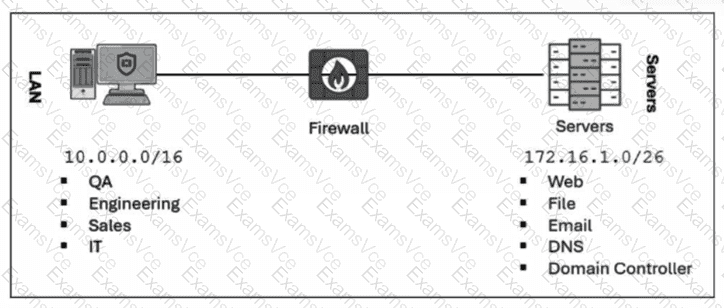
Definition of Attack Surface:The attack surface consists of all the different points where an attacker could try to enter data to or extract data from an environment. This includes hardware, software, SaaS components, and network interfaces.
Effectiveness of Asset Removal:Removing unused devices, services, or software is the most fundamental and effective way to reduce the attack surface. By decommissioning an unused server or workstation (as shown in the LAN/Server diagram), you completely eliminate all potential vulnerabilities associated with that asset, its operating system, and its active services.
Contrast with other methods:
Forwarding logs (A)andDeep Inspection (B)aredetectiveandpreventivecontrols, respectively. They help manage the risk within the existing attack surface but do not actually shrink the size of the surface itself.
Macrosegmentation (C)limits the "blast radius" or lateral movement after a compromise has occurred. While it secures the interior, it does not remove the initial entry points that define the external attack surface.
Why other options are incorrect:
Forwarding logs (A):This increases visibility but does not remove potential vulnerabilities.
Deep Inspection (B):This is a security measure to detect threats within existing traffic but does not eliminate the target (the device) itself.
Implement macrosegmentation (C):While highly recommended for security, it is a network architecture strategy to contain threats, whereas the prompt asks for the most effective method toreducethe surface. Removing the asset entirely (D) is the most absolute reduction possible.