CompTIA PT0-002 Question Answer
A penetration tester downloaded a Java application file from a compromised web server and identifies how to invoke it by looking at the following log:
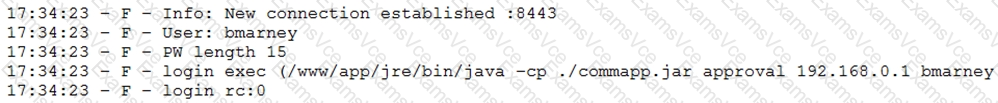
Which of the following is the order of steps the penetration tester needs to follow to validate whether the Java application uses encryption over sockets?
CompTIA PT0-002 Summary
- Vendor: CompTIA
- Product: PT0-002
- Update on: Mar 4, 2026
- Questions: 464



