The MicrosoftGraphActivityLogs table in Microsoft Defender XDR (formerly part of Microsoft 365 Defender and Microsoft Sentinel) records API activity involving the Microsoft Graph API. This includes calls made to endpoints that interact with Azure AD, Exchange Online, SharePoint, Teams, and other Microsoft 365 services.
According to Microsoft’s official documentation:
“The MicrosoftGraphActivityLogs table provides visibility into activities performed via Microsoft Graph API. These include directory enumeration, mailbox data access, policy queries, and user management actions. The table helps detect misuse of Graph API for reconnaissance or lateral movement.”
Here’s how it applies to the tactics listed:
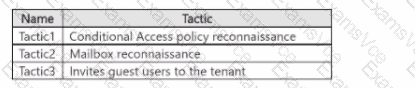
Tactic1 – Conditional Access policy reconnaissanceAttackers can use Graph API calls (e.g., GET /identity/conditionalAccess/policies) to enumerate Conditional Access policies. This activity is logged in MicrosoftGraphActivityLogs, showing which API endpoints were accessed, by whom, and when.
Tactic2 – Mailbox reconnaissanceUsing Graph API calls such as GET /users/{id}/messages, attackers can read or enumerate mailbox data. These API interactions are also captured within MicrosoftGraphActivityLogs, allowing analysts to correlate them to potential reconnaissance behavior.
Tactic3 – Invites guest users to the tenantGraph API requests like POST /invitations are used to invite external users (B2B collaboration). These events are also recorded in the same table, providing audit visibility into cross-tenant invitation attempts.
Because all three tactics — Conditional Access reconnaissance, mailbox reconnaissance, and guest user invitations — involve the Microsoft Graph API, they are all detectable through the MicrosoftGraphActivityLogs table.
Therefore, the verified correct answer is:
✅ D. Tactic1, Tactic2, and Tactic3