WGU Secure-Software-Design Question Answer
An individual is developing a software application that has a back-end database and is concerned that a malicious user may run the following SOL query to pull information about all accounts from the database:
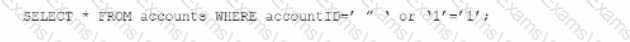
Which technique should be used to detect this vulnerability without running the source codes?
WGU Secure-Software-Design Summary
- Vendor: WGU
- Product: Secure-Software-Design
- Update on: Feb 21, 2026
- Questions: 118



