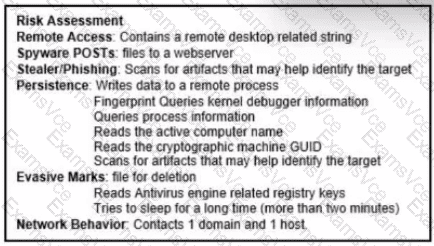
Comprehensive and Detailed Explanation:
The exhibit lists several behaviors under categories such as Remote Access, Stealer/Phishing, Persistence, and Evasive Marks. Notably, under “Persistence” it states:
This behavior is indicative of “process injection,” a technique where malware writes or injects malicious code into the address space of another process. This allows the malware to evade detection and run within the context of a legitimate process.
This matches the MITRE ATT&CK technique T1055 (Process Injection), which is also discussed in the Cisco CyberOps Associate guide under evasion and persistence tactics used by malware.
While modified registry and data compression are possible signs of malware, they are not explicitly referenced in the exhibit. The definitive indicator shown is related to process injection.
Therefore, the correct answer is: C. process injection.