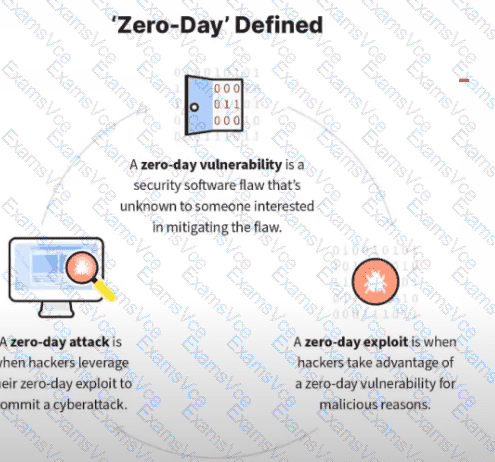
Azero-day vulnerabilityis typically not identifiable through a standard vulnerability assessment. Vulnerability scanners and routine assessments rely onknown vulnerability signatures, published advisories, and documented weaknesses. By definition, a zero-day vulnerability is unknown to vendors, defenders, and security tools at the time it exists or is exploited.
File permission issues, buffer overflows, and cross-site scripting (XSS) vulnerabilities are commonly detected through automated scans, configuration reviews, and application testing because they are well understood and documented classes of weaknesses. Scanners are specifically designed to identify these known issues.
Zero-day vulnerabilities, however, require alternative detection approaches such as behavioral monitoring, anomaly detection, threat intelligence, or post-exploitation forensics. This limitation is why vulnerability assessments alone are insufficient and must be complemented withdefense-in-depth, monitoring, and incident response capabilities.
Security frameworks consistently emphasize that organizations should not rely solely on vulnerability scanning, as it cannot detect unknown or newly emerging threats like zero-day vulnerabilities.