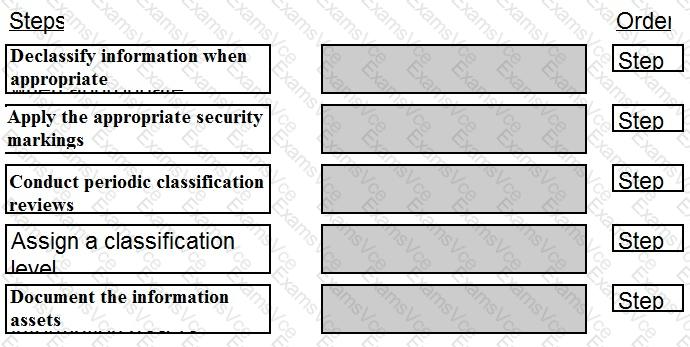
The following information classification steps should be placed in sequential order as follows:
Information classification is a process or a method of categorizing the information assets based on their sensitivity, criticality, or value, and applying the appropriate security controls or measures to protect them. Information classification can help to ensure the confidentiality, the integrity, and the availability of the information assets, and to support the security, the compliance, or the business objectives of the organization. The information classification steps are the activities or the tasks that are involved in the information classification process, and they should be performed in a sequential order, as follows:
Document the information assets: This step involves identifying, inventorying, and describing the information assets that are owned, used, or managed by the organization, such as the data, the documents, the records, or the media. This step can help to determine the scope, the ownership, or the characteristics of the information assets, and to prepare for the next steps of the information classification process.
Assign a classification level: This step involves assigning a classification level or a label to each information asset, based on the sensitivity, the criticality, or the value of the information asset, and the impact or the consequence of the unauthorized or the malicious access, disclosure, modification, or destruction of the information asset. The classification level or the label can indicate the degree or the extent of the security protection or the handling that the information asset requires, such as the confidentiality, the integrity, or the availability. The classification level or the label can vary depending on the organization’s policies, standards, or regulations, but some common examples are public, internal, confidential, or secret.
Apply the appropriate security markings: This step involves applying the appropriate security markings or indicators to the information assets, based on the classification level or the label of the information assets. The security markings or indicators can include the visual, the physical, or the electronic symbols, signs, or codes that show the classification level or the label of the information assets, such as the banners, the headers, the footers, the stamps, the stickers, the tags, or the metadata. The security markings or indicators can help to communicate, inform, or remind the users or the entities of the security protection or the handling that the information assets require, and to prevent or reduce the risk of the unauthorized or the malicious access, disclosure, modification, or destruction of the information assets.
Conduct periodic classification reviews: This step involves conducting periodic classification reviews or assessments of the information assets, to ensure that the classification level or the label and the security markings or indicators of the information assets are accurate, consistent, and up-to-date. The periodic classification reviews or assessments can be triggered by the changes or the events that affect the sensitivity, the criticality, or the value of the information assets, such as the business needs, the legal requirements, the security incidents, or the data lifecycle. The periodic classification reviews or assessments can help to verify, validate, or update the classification level or the label and the security markings or indicators of the information assets, and to maintain or improve the security protection or the handling of the information assets.
Declassify information when appropriate: This step involves declassifying or downgrading the information assets when appropriate, to reduce or remove the security protection or the handling that the information assets require, based on the sensitivity, the criticality, or the value of the information assets, and the impact or the consequence of the unauthorized or the malicious access, disclosure, modification, or destruction of the information assets. The declassification or the downgrade of the information assets can be triggered by the changes or the events that affect the sensitivity, the criticality, or the value of the information assets, such as the expiration, the disposal, the release, or the transfer of the information assets. The declassification or the downgrade of the information assets can help to optimize, balance, or streamline the security protection or the handling of the information assets, and to support the security,