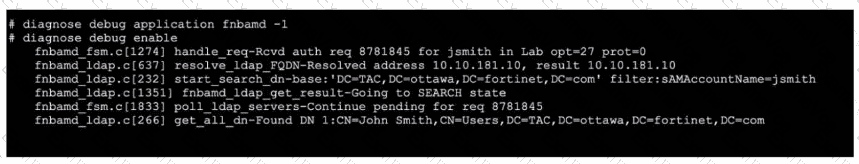
According to Fortinet’s LDAP authentication workflow as described in the FortiOS Administration Guide and the official LDAP debug log interpretation, each authentication attempt is split into several key steps: Bind Request, Search Request, and then, if successful, a Bind as the found user DN. In the provided debug output, we see "start search_dn-base" with a filter "sAMAccountName=jsmith" and the log line "Going to SEARCH state," confirming that FortiOS is in the second step—the Search Request (Option D). Official documentation highlights this exact phrase "SEARCH state" as indicative of Step 2 within the LDAP process (“Bind → Search → Bind”).
Additionally, the last line “Found DN 1: CN=John Smith, CN=Users, DC=TAC, DC=ottawa, DC=fortinet, DC=com” verifies that the system has successfully mapped the username to the Distinguished Name (DN) and this user is “John Smith.” The authentication will now proceed using this mapped user (Option B). Fortinet’s logs record the found DN after a successful search, which is a strong confirmation that the user’s credentials can be validated against the found DN.
Options A and C are not supported directly by the debug output shown:
The server name "Lab" is referenced as part of the request, but not explicitly as the LDAP server’s configured name in this output.
Step 3 (Bind Request) would follow finding the DN, but the log here demonstrates the Search and DN found—per Fortinet, this precedes the actual Bind/validation step.
[References:, FortiOS Administration Guide: LDAP Authentication Process and Debug Logs, Fortinet Official KB: LDAP Integration Workflow and Log Interpretation, , ]