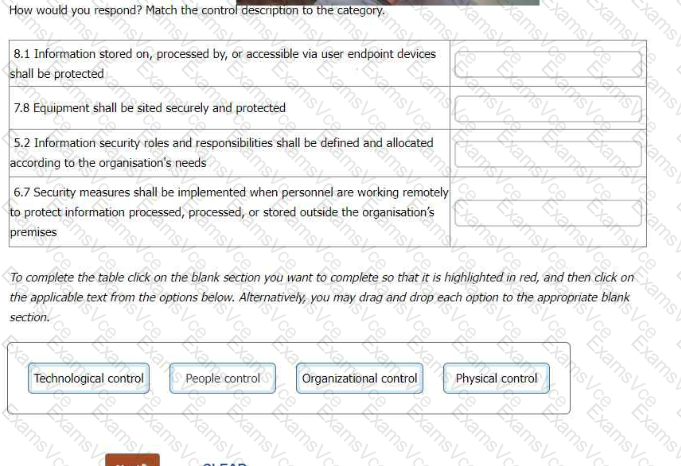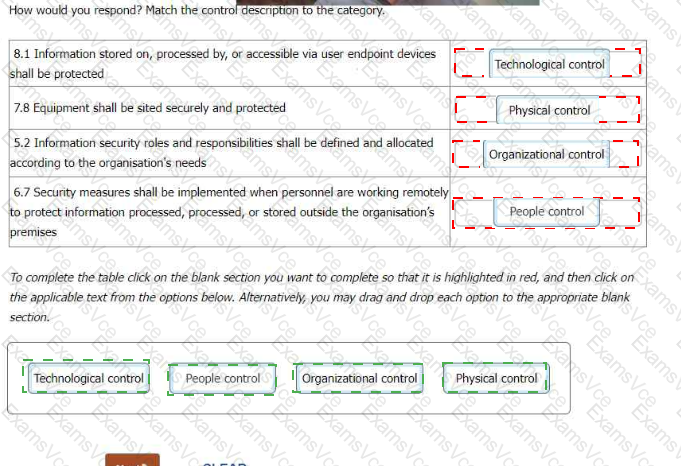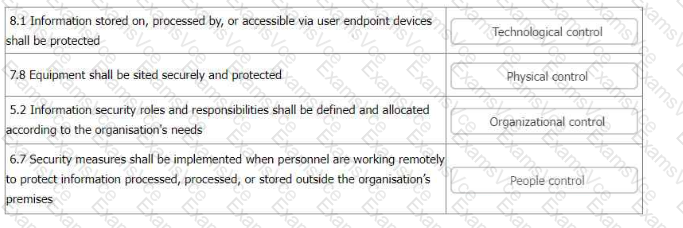
8.1 Information stored on, processed by, or accessible via user endpoint devices shall be protected = Technological control 7.8 Equipment shall be sited securely and protected = Physical control 5.2 Information security roles and responsibilities shall be defined and allocated according to the organisation’s needs = Organisational control 6.7 Security measures shall be implemented when personnel are working remotely to protect information processed, processed, or stored outside the organisation’s premises = People control
Explanation: According to the web search results from my predefined tool, ISO 27001:2022 has restructured and consolidated the Annex A controls into four categories: organisational, people, physical, and technological12. These categories reflect the different aspects and dimensions of information security, and are aligned with the cybersecurity concepts of identify, protect, detect, respond, and recover3. The controls in each category are as follows4:
Organisational controls: These are controls that relate to the governance, management, and coordination of information security activities within the organisation. They include controls such as information security policies, roles and responsibilities, risk assessment and treatment, performance evaluation, and improvement.
People controls: These are controls that relate to the behaviour, awareness, and competence of the people involved in information security, both within and outside the organisation. They include controls such as human resource security, training and awareness, access control, incident management, and business continuity.
Physical controls: These are controls that relate to the protection of physical assets and environments that store, process, or transmit information. They include controls such as physical security, environmental security, equipment security, and media security.
Technological controls: These are controls that relate to the use of technology to implement, monitor, and maintain information security. They include controls such as cryptography, network security, system security, application security, and threat intelligence.
Based on these categories, the controls listed in the question can be matched as follows:
8.1 Information stored on, processed by, or accessible via user endpoint devices shall be protected: This is a technological control, as it involves the use of technology to protect information on devices such as laptops, smartphones, tablets, etc. It may include measures such as encryption, authentication, antivirus, firewall, etc.
7.8 Equipment shall be sited securely and protected: This is a physical control, as it involves the protection of physical assets and environments that store, process, or transmit information. It may include measures such as locks, alarms, CCTV, fire suppression, etc.
5.2 Information security roles and responsibilities shall be defined and allocated according to the organisation’s needs: This is an organisational control, as it involves the governance, management, and coordination of information security activities within the organisation. It may include measures such as defining the authority and accountability of information security personnel, establishing reporting lines and communication channels, assigning tasks and duties, etc.
6.7 Security measures shall be implemented when personnel are working remotely to protect information processed, processed, or stored outside the organisation’s premises: This is a people control, as it involves the behaviour, awareness, and competence of the people involved in information security, both within and outside the organisation. It may include measures such as providing guidance and training on remote working, enforcing policies and procedures, monitoring and auditing remote activities, etc.
References: = 1: A Breakdown of ISO 27001:2022 Annex A Controls - BARR Advisory42: ISO 27001:2022 Annex A Controls - What’s New? | ISMS.Online13: How many controls are there in ISO 27001:2022? - Strike Graph34: ISO/IEC 27001:2022 Information technology — Security techniques — Information security management systems — Requirements, Annex A.