PECB ISO-IEC-27001-Lead-Auditor Question Answer
You are performing an ISMS audit at a residential nursing home called ABC that provides healthcare services.
The next step in your audit plan is to verify the information security of ABC's healthcare mobile app development, support, and lifecycle process. During the audit, you learned the organisation outsourced the mobile app development to a professional software development organisation with CMMI Level 5, ITSM
(ISO/IEC 20000-1), BCMS (ISO 22301) and ISMS (ISO/IEC 27001) certified.
The IT Manager presents the software security management procedure and summarises the process as follows:
The mobile app development shall adopt "security-by-design" and "security-by-default" principles, as a minimum. The following security functions for personal data protection shall be available:
Access control.
Personal data encryption, i.e., Advanced Encryption Standard (AES) algorithm, key lengths: 256 bits; and
Personal data pseudonymization.
Vulnerability checked and no security backdoor
You sample the latest Mobile App Test report - Reference ID: 0098, details as follows:
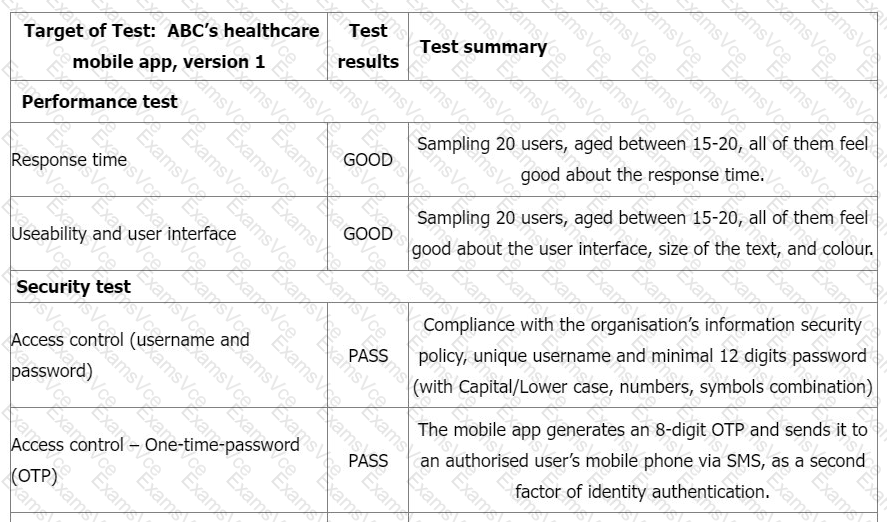

You would like to investigate other areas further to collect more audit evidence. Select three options that will not be in your audit trail.
PECB ISO-IEC-27001-Lead-Auditor Summary
- Vendor: PECB
- Product: ISO-IEC-27001-Lead-Auditor
- Update on: Feb 1, 2026
- Questions: 418



